Every single day the amount of Javascript packages is growing. It is the result of a community’s activity, which, on one hand, demands new solutions, on the other – generates them as a form of self-development or realization. Such large growth opens new doors and possibilities, but also brings danger, which every developer has to be aware of.
In late November 2018, the GitHub community reported of a serious vulnerability in event-stream – package that helps working with node events more efficiently. It was fairly popular, as amount of downloads in that specific period was reaching over 2.2 mln per week (in comparison to React with 3,7 mlns). Event-stream, as well as its dependencies, were dependent on another library – flatmap-steam, that happened to have been updated with a crypto-pocket malware. It allowed stealing private keys and other details from the users’ accounts on machines where the package was bundled.
Eventually, flatmap-stream was removed from NPM, which created temporal problems with many other libraries. In May, the same year, the community found a backdoor within the getcookie package, which was part of many other dependencies as well. Such examples can be multiplied, which demonstrates that it is important to pay attention to dependencies installed into a project, not only from the Javascript perspective, but also in a general context.
Rely on official solutions and large communities
As far as possible it is important to rely on official solutions in your project. They are not just less vulnerable because of a better development process. A large community, which usually comes with a better brand, helps identify problems much faster and, what is more important – find good solutions.
Use NPM trends
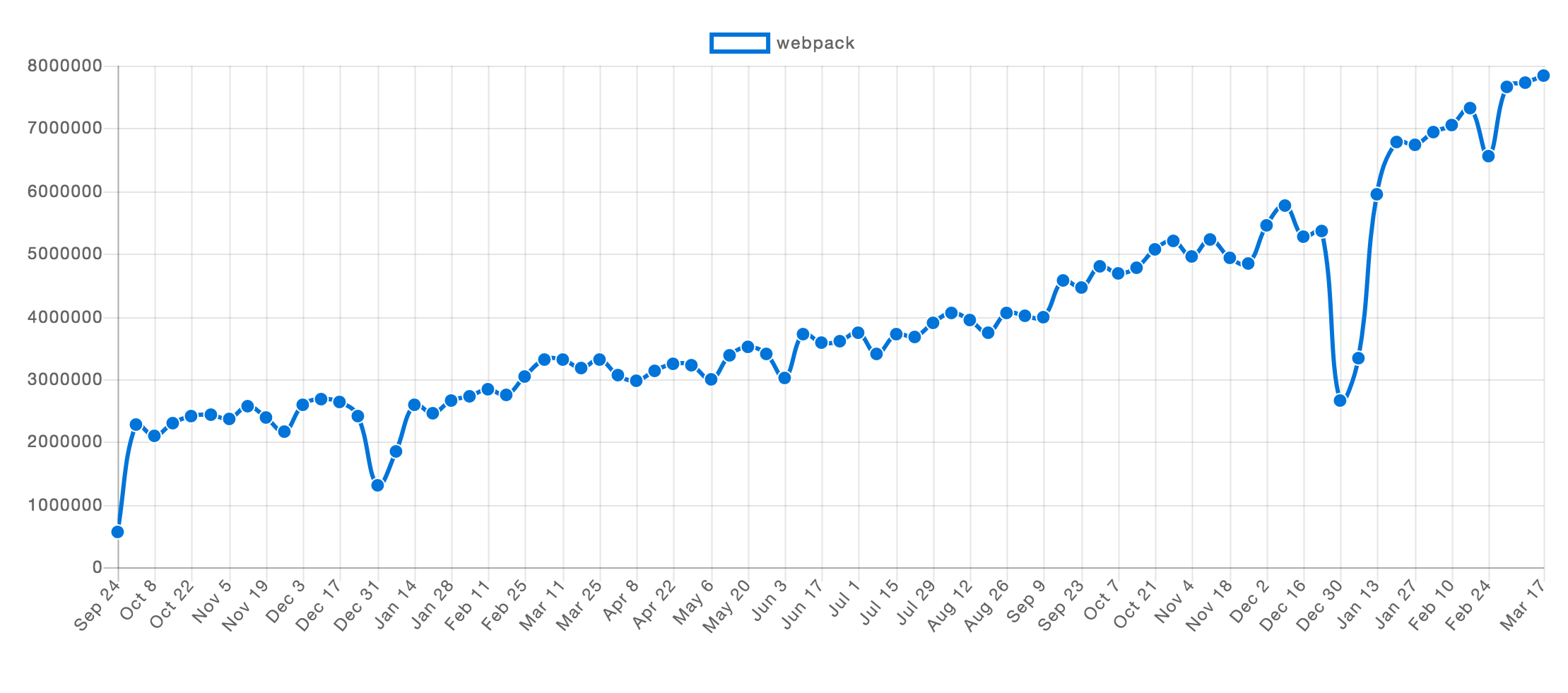
Fig. 1 Webpack NPM trend.
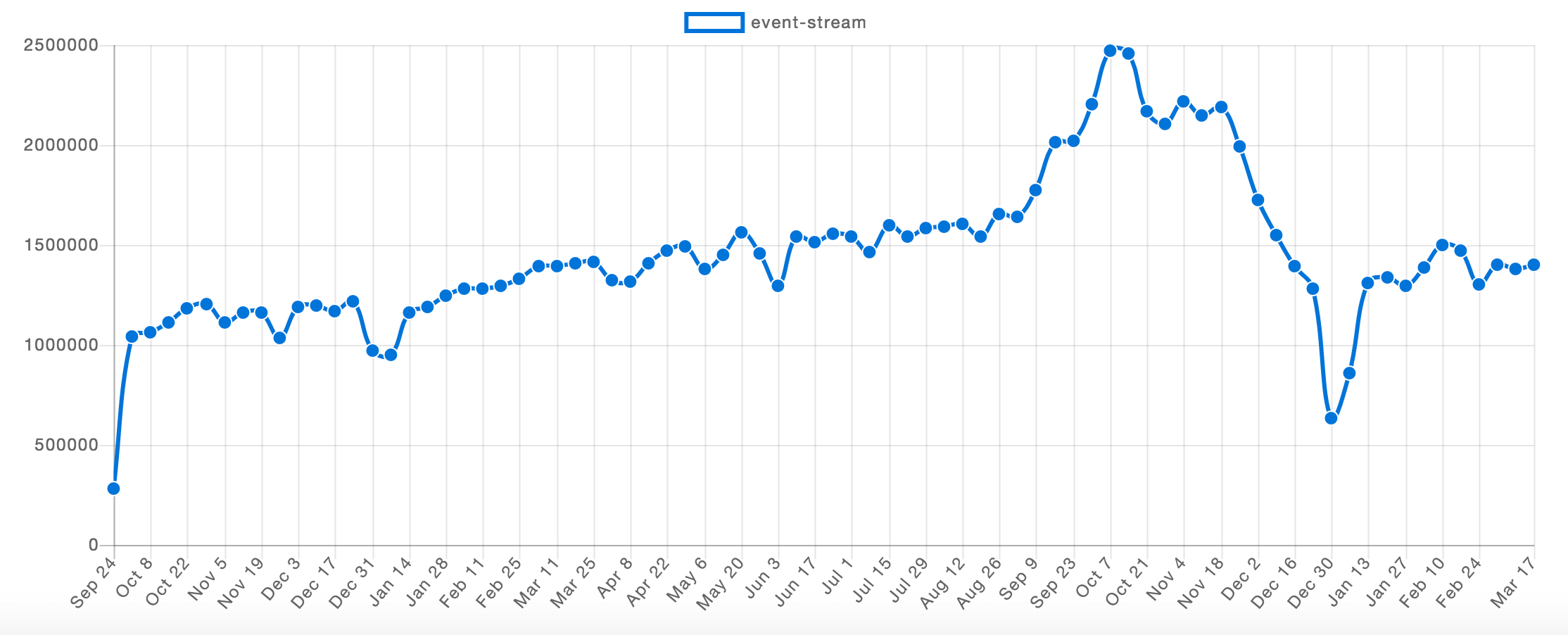
Fig. 2. Event-stream NPM trend.
Sometimes, knowledge of a current state of the package may not represent their past. A quick look at the npm trends chart can show you an actual package trending. It will show not only large peaks, where some vulnerability could be found, but the general condition of a given package (NOTE: large peaks on google trends near 24 – 30 December represents holiday season, which may not necessarily represent a problem). As an example, take a look at figure 1 – a representing trend of Webpack download per week. You will see stable growth without any breaking points, which may suggest that Webpack is a stable and secure package to use. On the other hand, on figure 2 you will find a large drop in November, which is a clear signal that something wrong could have happened in that period (which we already know is true).
Dependency audit
The best and most reliable way to verify the state of your dependencies is to perform an audit. This command is now available natively both for yarn and npm, although it requires their latest versions. It sends a list of current dependencies into a proper endpoint and returns information containing their current vulnerabilities and other details of usage, including reference to documentation. (figure3).
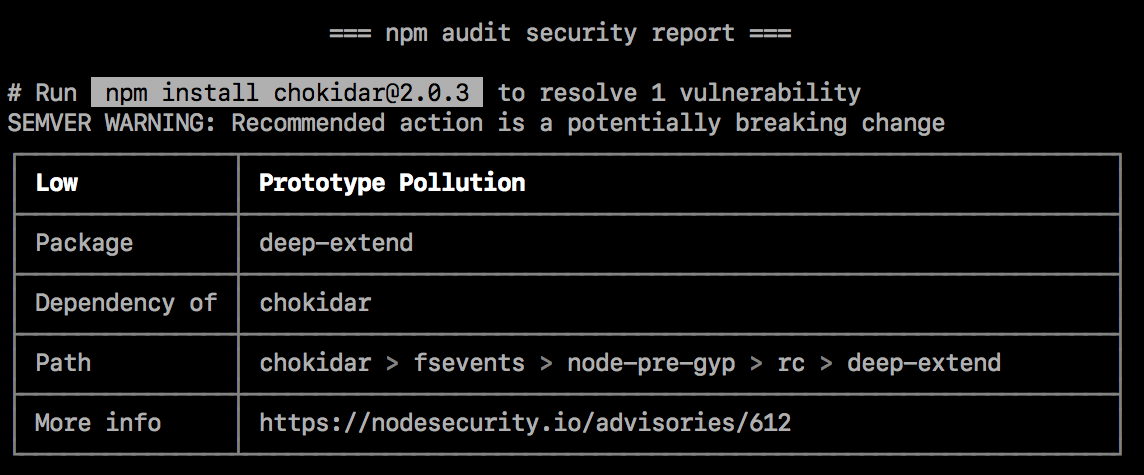
Fig. 3. Example of npm audit command result. Source: https://docs.npmjs.com
Managing dependencies in Javascript is not an easy task. A number of solutions are growing every day, therefore remember to choose your dependencies wisely and carefully. Keep on auditing your current project and update your packages regularly.
To learn more about javascript dependencies and how to resolve some of their problems, please check this article.
Source:
- https://github.com/dominictarr/event-stream/issues/116
- https://blog.npmjs.org/post/180565383195/details-about-the-event-stream-incident
- https://blog.npmjs.org/post/173526807575/reported-malicious-module-getcookies
- https://docs.npmjs.com/auditing-package-dependencies-for-security-vulnerabilities
- https://docs.npmjs.com/cli/audit
- https://yarnpkg.com/lang/en/docs/cli/audit/